By Dave Kelly, CTO
SensCy
We all understand that the last few years have been a difficult time for many small businesses. The pandemic brought uncertainty, financial strain and a lot of sleepless nights. But small business owners are resilient and have managed to change the way in which we do business to survive—and thrive—in this new era. As a result, our workforces have become a bit more distributed, with less time in an office and more time working from home.
As we continue to transition into our new normal, there is another risk on the horizon that cannot be ignored. According to Cybersecurity Magazine, 61% of small to medium-sized businesses (SMB) have reported at least one cyberattack during the previous year and 43% of all data breaches now involve SMBs. While these statistics are alarming, the good news is that there are many cost-effective things that can be done to significantly reduce the risk of a successful attack and/or ensure the ability to recover should an incident occur. In this series of articles, I will touch on what small businesses can do to help mitigate this risk.
EMPLOYEE TRAINING
We can all agree that our employees are our greatest asset. But when it comes to cybersecurity, they can also be our greatest risk. Researchers at Stanford University found that 88% of all data breaches are caused by an employee making a mistake. This has been a consistent trend in cybersecurity for many years, but it can be avoided with persistent cybersecurity awareness and policy training for our employees.
For context to this problem, let’s examine one of the many ways in which hackers attempt to trick our employees into making a mistake.
PHISHING
Phishing is a form of social engineering and is a common technique used by hackers to trick employees into divulging company information or to download malicious code. This technique takes advantage of two traits that all our best employees have: trust and a desire to help others.
Phishing attacks can occur through email, text messages, instant messaging, social media or phone calls. The common thread of a phishing attack is to present an immediate problem to our employee and ask for their help to solve it. Below is an example:
The hacker sends a text message that looks like it is coming from a supervisor or co-worker.
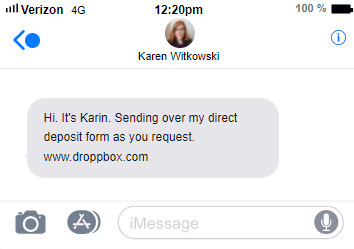
The link in this message contains malicious code that, when clicked on, is immediately downloaded to the employee’s device. If the right protections are not in place, it can spread throughout your entire network.
How easy is it for hackers to pull off this type of social engineering?
I sent this message using a Spoofing tool. The tool enabled me to change my phone number and contact name to that of Karen Witkowski (our new marketing manager at SensCy). I then went to LinkedIn and downloaded a photo of Karen. I uploaded that image to the Spoofing tool and what you see is the result. When people change jobs, they announce it on LinkedIn. Hackers view this information as an opportunity to trick your employee into making a mistake.
According to a recent report in Forbes, employees of small businesses with less than 100 employees will experience 350% more social engineering attacks than employees of larger enterprises. Why is this happening so frequently? Hackers have realized that small business employees are less prepared to deal with these situations due to a lack of consistent training on how to identify social engineering.
There are a few clues in the above message that, with the proper training, employees will recognize:
- First, there are two errors in the text. Karen is spelled incorrectly and the phrase “as you request” should be “at your request” or “as you requested.” Foreign actors are often behind these types of attacks and being non-native speakers of English, they regularly make these types of mistakes.
- The link appears to be a Dropbox link. SensCy does not use Dropbox in our day-to-day business.
- If you look closely at the link, there is an extra “p.” The correctly spelled link would be dropbox.com.
Recognizing these cyberattack attempts requires that you commit to a persistent training program. Employees can become very adept at identifying these fraudulent attempts with practice. Studies have demonstrated that we humans become experts through repetition. SensCy recommends a cybersecurity training program that involves 10 to 15-minute lessons every other month.
It’s important to remember that these attacks are targeting your best employees—the ones who are trustworthy and want to help their teammates. By committing to a cybersecurity education program, you can protect your greatest asset (your employees), safeguard your business and sleep better at night knowing you are creating a front-line defense against cyber criminals.
SBAM members have access to a cost-effective strategy that can significantly reduce your risk and ensure your business will recover should an attack occur. Visit www.sbam.org/cybersecurity or call the SBAM membership team at (800) 362-5461 for more information.
BIO:
Dave Kelly is the CTO of SensCy, a cybersecurity start-up in Ann Arbor, Michigan focused on helping small and medium-sized organizations improve their cyber health. Dave served 26 years with the Michigan State Police (MSP), where he was the commanding officer of the Michigan Cyber Command Center and the Michigan Intelligence Operations Center. Dave retired from the MSP as an enlisted Captain and the Director of Technology.
Since retiring from the MSP, Dave has served as a VP of Solutions & Strategy and as a Chief Solutions Officer for two major software companies. In these roles, Dave led projects that applied machine learning and Artificial Intelligence to cyber data to empower SOC analysts and threat incident response while informing Zero Trust Architecture.
Dave has been a keynote speaker, expert panelist and subject matter expert for diverse government audiences and is a veteran of the United States Marine Corps.